Author: @Ambulong
phpMyAdmin is a well-known MySQL/MariaDB online management tool, phpMyAdmin team released the version 4.7.7 that addresses the CSRF vulnerability found by Barot. (PMASA-2017-9). The vulnerability allows an attacker to execute an arbitrary SQL statement silently by inducing an administrator to access malicious pages.
1 phpMyAmin 4.7.x XSRF/CSRF Vulnerability (PMASA-2017-9)
phpMyAdmin is a well-known MySQL/MariaDB online management tool, phpMyAdmin team released the version 4.7.7 that addresses the CSRF vulnerability found by Barot. (PMASA-2017-9). The vulnerability allows an attacker to execute an arbitrary SQL statement silently by inducing an administrator to access malicious pages.
In this article, we will use VulnSpy’s online phpMyAdmin environment to demonstrate the exploit of this vulnerability.
VulnSpy’s online phpMyAdmin environment address: https://www.vulnspy.com/?u=pmasa-2017-9
2 Exploit CSRF - Modifying the password of current user
Change the current user password to www.vulnspy.com, SQL command:
|
|
Exploit Demonstration
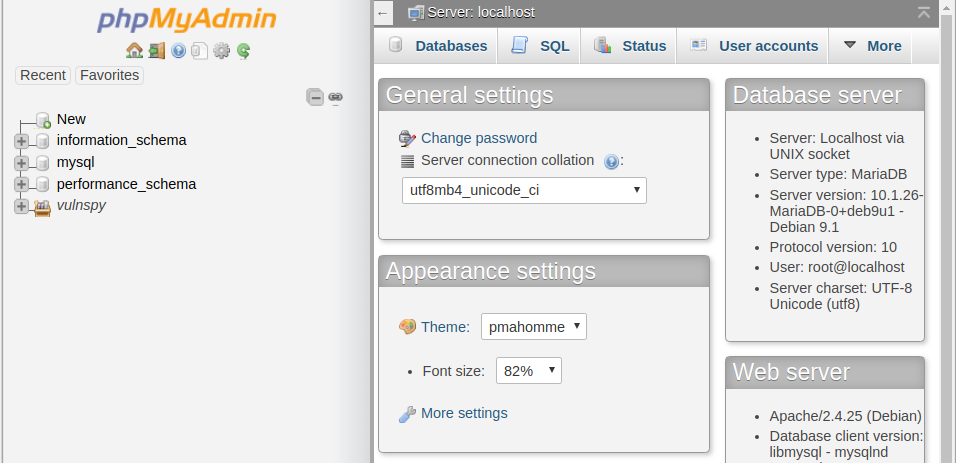
2.1 Log in to phpMyAdmin
Username: root Password: toor
2.2 Create a page with malicious code.
Filename: 2.payload.html
|
|
2.3 Open the file 2.payload.html in browser
Go back to phpMyAdmin, you’ll find that the account has been loged out automatically, and the password of root have been changed.
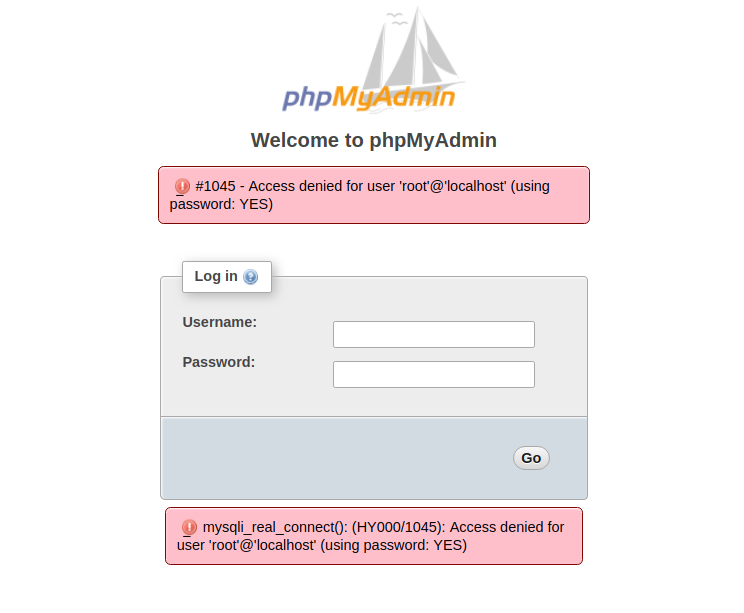
2.4 Login successfully with the password www.vulnspy.com
3 Exploit CSRF - Arbitrary File Write
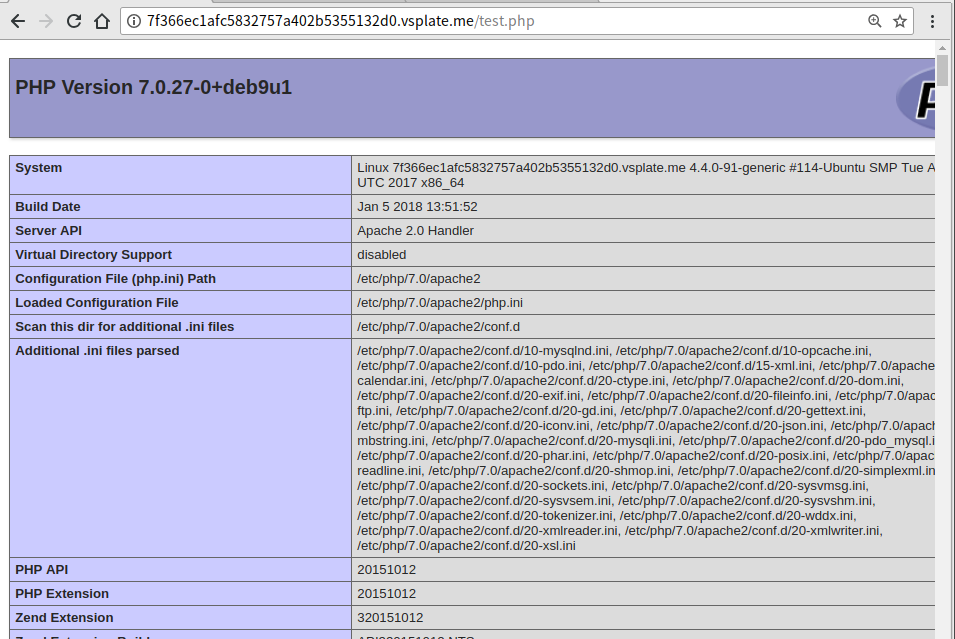
Write the code <?php phpinfo();?> to the file /var/www/html/test.php, SQL command:
|
|
Exploit Demonstration
3.1 Payload
|
|
3.2 Open the file contain the payload in browser
3.3 Visit test.php
4 Exploit CSRF - Data Retrieval over DNS
Steal the password hash of root, SQL command:
|
|
Fetch the current database name:
|
|
VSPlate not supports this exploit
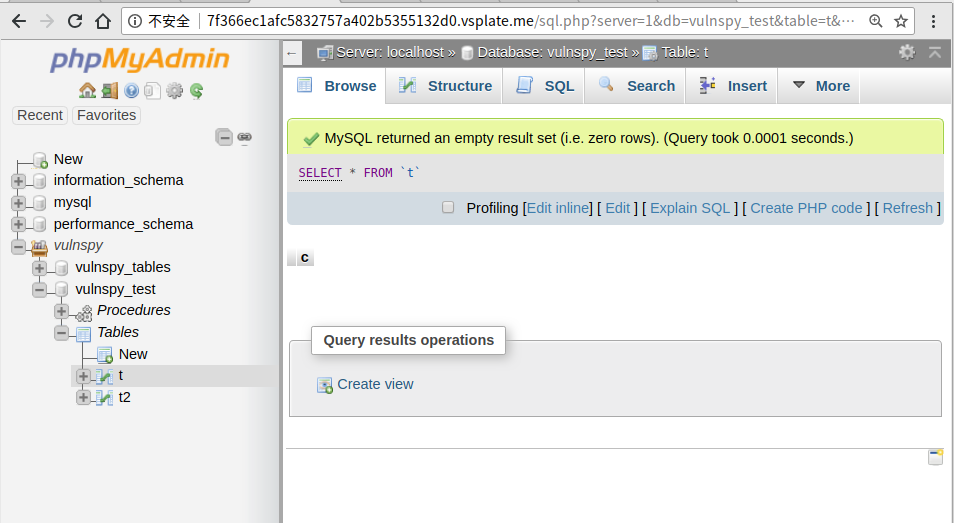
5 Exploit CSRF - Empty All Rows From All Tables
Empty all rows from all tables, SQL command:
|
|
Exploit Demonstration
5.1 Payload
|
|
5.2 Open the file contain the payload in browser
5.3 Go back to phpMyAdmin
You’ll find the data in database vulnspy_tables and vulnspy_test have been deleted.