作者:@Ambulong
在上一篇文章 Wordpress SQL注入分析(一) 中,我们分析了Wordpress中的prepare函数在什么情况下会产生SQL注入漏洞。本篇文章将分析Wordpress中的一处SQL注入。
在上一篇文章 Wordpress SQL注入分析(一) 中,我们分析了Wordpress中的prepare函数在什么情况下会产生SQL注入漏洞。本篇文章将分析Wordpress中的一处SQL注入。
当前最新版:Wordpress 4.8.1
第三章:发现Wordpress中的SQL注入
3.1 SQL注入分析
在delete_metadata函数(文件:/wp-includes/meta.php)中存在如下代码:
|
|
我们来看下关键部分代码:
|
|
按我们上一篇文章的分析,若$meta_value可控,此处就存在SQL注入漏洞。而$meta_value变量是作为参数从外部传进来的,所以我们需要查找调用到delete_metadata函数,且第四个参数可控的地方。
我们此处直接选用@slavco文章中的wp_delete_attachment函数(文件:/wp-includes/post.php),代码如下:
|
|
关键代码:
|
|
里面的$post_id同样从外部传入,所以我们继续查找调用到wp_delete_attachment函数,且第一个参数可控的地方。
在文件/wp-admin/edit.php中有个比较明显的调用点,且$post_id(即:wp_delete_attachment函数的第一个参数)可控。
3.2 利用条件分析
我们首先简单地整理下相关文件/函数的调用过程与调用条件。
1. 文件:/wp-admin/edit.php
|
|
需满足条件:
- $doaction = $wp_list_table->current_action() = ‘delete’
即:$_REQUEST[‘action’] = ‘delete’ - 通过check_admin_referer(‘bulk-posts’)
检查$_REQUEST[‘_wpnonce’] - $post_ids = $_REQUEST[‘media’] = ‘%1$%s abc’
传入测试注入字符串 - current_user_can( ‘delete_post’, $post_id ) == true
当前用户是否有删除该文章权限 - $post_del->post_type == ‘attachment’
该文章类型为attachment,可通过添加媒体功能添加
2. 文件:/wp-includes/post.php
|
|
需满足条件:
- $post_id对应的文章存在
因为有类型转换,所以可以用$post_id = '123 %1$%s abc'绕过。(转换为整数后$post_id = 123) - $post_id对应的文章类型为attachment
3. 文件:/wp-includes/meta.php
|
|
需满足条件:
- “SELECT meta_id FROM wp_postmeta WHERE meta_key = ‘_thumbnail_id’ AND meta_value = ‘xxx’”存在
即:需要使得wp_postmeta表内的_thumbnail_id的内容与我们的SQL语句一样(即内容为’123 %2$%s abc’)。
wp_postmeta表内的meta_key和meta_value字段是可通过写文章功能内的自定义栏目添加的。但是禁止添加名称以下划线开头的自定义栏目,所以正常情况下我们无法添加_thumbnail_id栏目。
关于如果绕过下划线检查添加post meta,请见下一篇文章:
3.3 SQL注入漏洞利用
- 添加媒体(/wp-admin/media-new.php),并记住媒体ID(这里的ID是55)。
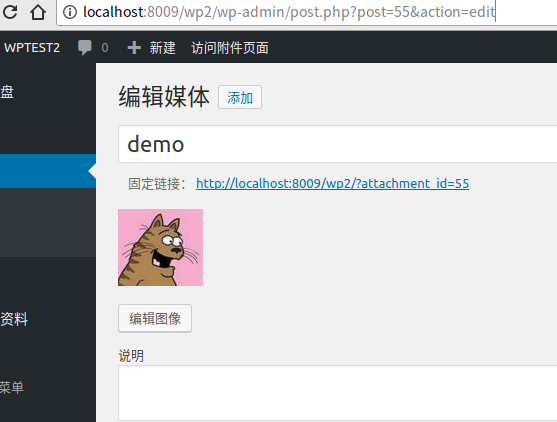
- 获取_wpnonce。
打开/wp-admin/edit.php?post_type=post,找到posts-filter内的_wpnonce(这里的_wpnonce是301ee97c09)
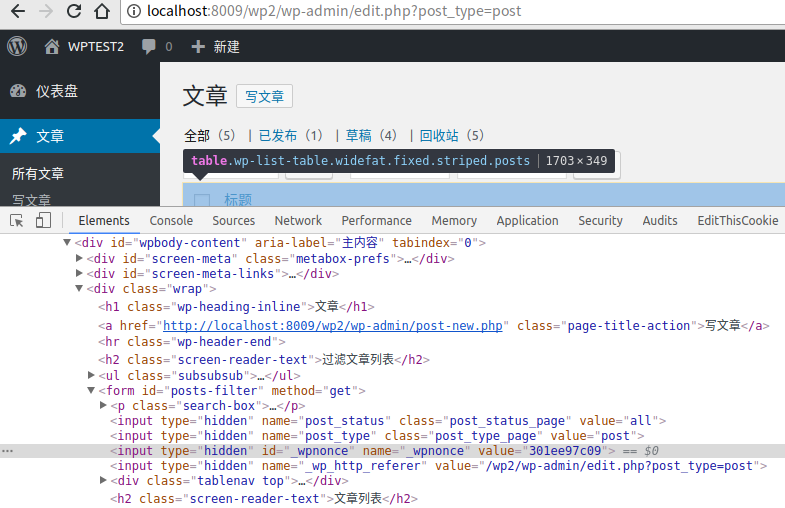
添加/修改POST META,使存在meta_key为’_thumbnail_id’的meta_value为
'55 %1$%s or sleep(10)#'访问
/wp-admin/edit.php?action=delete&_wpnonce=301ee97c09&ids=55 %1$%s or sleep(10)#,触发SQL注入漏洞